Date:
21 Dec 2023
Author:
PREO AG
On-Premise vs. Cloud
Why cloud risks are almost always also company risks
Cloud solutions play a central role in the digital transformation of our economy. However, with the great economic opportunities that new cloud-based technologies open up for many companies, the risks inevitably increase, for instance through vendor lock-in, cloud sprawl or cyber attacks from the cloud. It is no coincidence that the Allianz Risk Barometer 2022 identified the following two business risks as the greatest worldwide: Concerns about unauthorised access to central and sensitive company data and the resulting operational restrictions or even business failures.
In addition, the Shadowserver Foundation currently reports that almost 20,000 Microsoft Exchange servers on the public Internet, more than half of which are in Europe, have reached the end of support, including Exchange versions 2007 (275 servers), 2010 (4062 servers) and 2013 (26,298 servers). This creates critical security vulnerabilities, including CVE-2021-26855, which make these servers vulnerable to remote code execution. Statistics suggest that many companies and organisations have not yet updated their servers despite the end of support.
The PREO licence experts therefore strongly recommend,
1. Check all Microsoft Exchange servers and update them if necessary,
2. Immediately patch any vulnerable systems identified
3. If updates are no longer possible, to switch to newer Exchange versions, bearing in mind that used licences can be a cost-effective alternative that can significantly reduce the burden on the IT budget.
In the following article, we show why cloud risks are not just IT risks, but also business risks, what needs to be considered when managing the most important risk factors and how companies can benefit from the integration of used on-premise software.
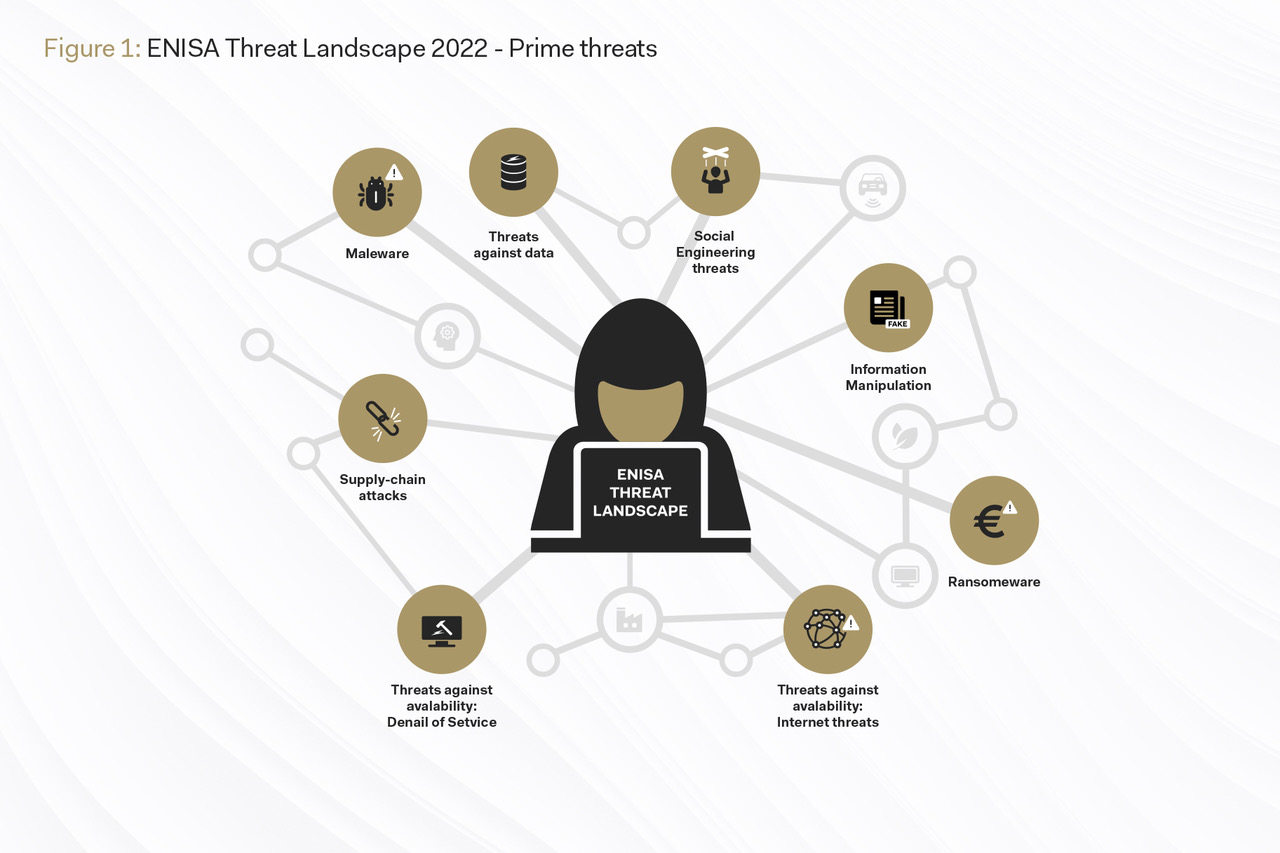
Top threats in cyberspace are also cloud risks
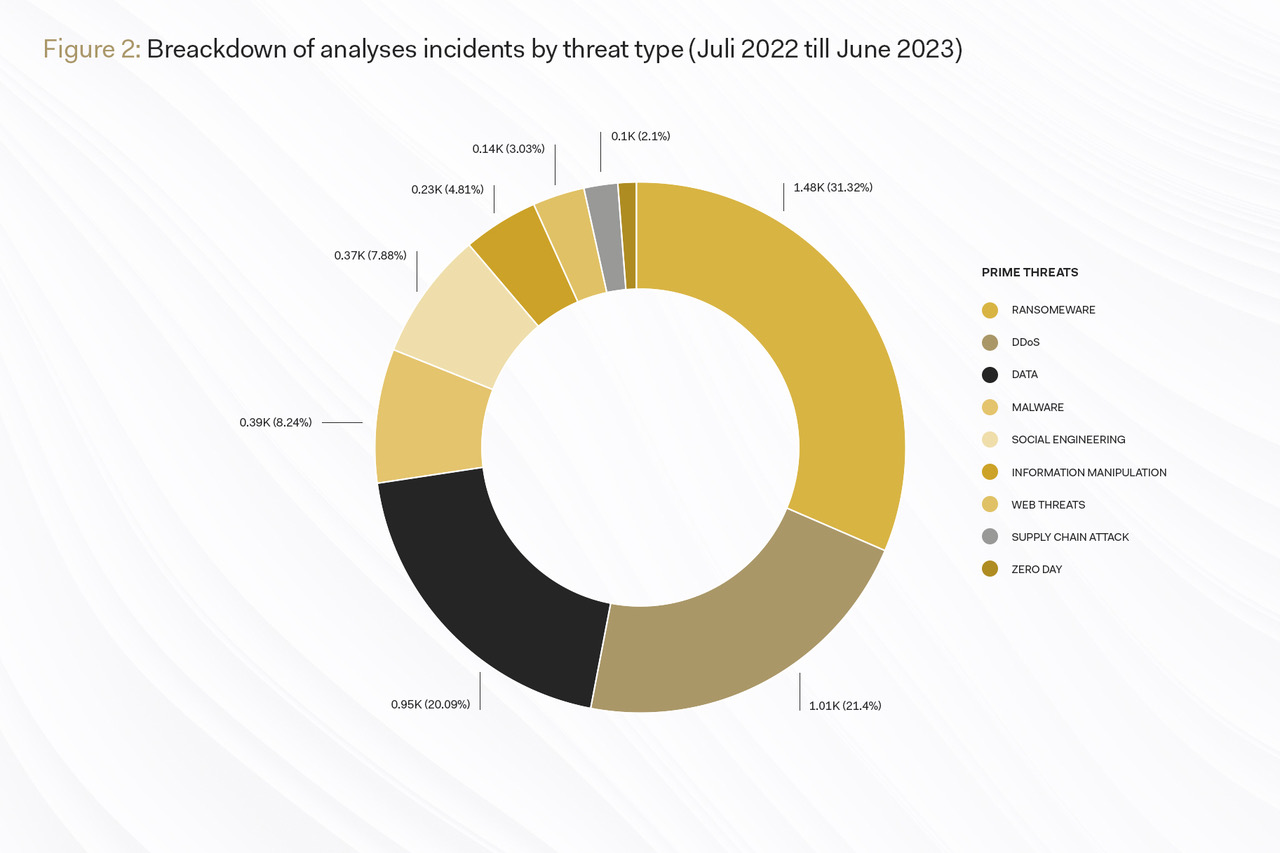
If you take a look at the latest "ENISA Threat Landscape 2023" report published by the EU cybersecurity agency, you will find that the biggest threats include those that pose a corresponding risk to the cloud. Broken down to the actual events in the period from July 2022 to June 2023, it stands out that the two most common threats, ransomware and threats against availability, determine more than 50 per cent of the risk potential.
The probability of falling victim to a ransomware attack, in which data is encrypted in a criminal manner, is therefore the highest in comparison. Many ransomware attacks target cloud services and cloud backups.
The threat to availability and integrity is also a frequent target, with attempts being made to either manipulate cloud data and thus jeopardise its integrity or to overload cloud services (distributed denial of service, or DDoS for short) in such a way that availability is threatened, temporarily restricted or even completely interrupted. Even large cloud providers such as Microsoft have already been confronted with such a scenario. According to the technology giant, the cause of the outages of the cloud web portals Azure, Outlook, OneDrive and MS Teams in June 2023 was presumably a DDoS attack by the hacker group Storm-1359, also known as ‘Anonymous Sudan’. Microsoft subsequently raised the security standards of its cloud services once again.
Other cyber risks that also represent a cloud risk at any time are malware,, and supply chain attacks, i.e. attacks on the cloud supply chain in which several service providers supply individual components for a cloud service.
Identify and actively manage cloud risks
However, the corporate risk assessment when using cloud services does not only include external risk defence. Comprehensive cloud risk management also includes the factors of compliance and IT security standards that directly affect the cloud. When it comes to compliance, it is particularly important to know the responsibilities and react accordingly. In terms of data protection under the General Data Protection Regulation (GDPR), for example, cloud services are categorised as order processing, meaning that the user as the client is responsible for ensuring that the respective provider complies with the relevant security standards. Before concluding a licence agreement, it is therefore essential to check this accordingly and to obtain proof of the standards in the form of commissioned data processing.
In Germany, the Federal Office for Information Security (BSI) has published a catalogue of requirements that is regularly updated to reflect current developments. The so-called C5 catalogue of criteria defines minimum requirements for secure cloud computing*, which is aimed at professional cloud providers, their auditors and customers. The C5 catalogue is therefore an important tool for selecting a suitable cloud provider and, according to the BSI, a practical basis for effective corporate risk management.
Cloud risk management - what companies should consider
Die digitale Transformation sorgt bereits heute dafür, dass Cloud-Risiken immer mehr zu unternehmerischen Risiken werden. Deshalb ist es erforderlich, das Cloud-Risikomanagement in das übergreifende Risikomanagement zu integrieren. Die Cloud Security Alliance (CSA) hat untersucht, welche Anforderungen ein Cloud Risk Management erfüllen muss. Unternehmen sollten sich dabei Fragen stellen wie:
- What risk management methods are already implemented in the organisation and are these suitable for managing risks in the cloud?
- Are all organisational stakeholders aware of the shared responsibility model introduced by cloud computing and are responsibilities appropriately reflected in risk management processes and programmes?
- Are all organisational units aware of the concepts and implications of indirect loss of control introduced by cloud computing, including the challenges to be considered for risk mitigation and validation?
- Are all organisational leaders sufficiently aware of the impact of cloud computing on the proliferation of their supply chains and how difficult it is to assess and monitor the consolidated residual third/third party risk?
- Are current compliance arrangements adequate to identify, assess and report the relevant cloud risks to relevant stakeholders?
For most companies, cloud computing offers numerous collaborative, cross-location benefits and practical solutions for a future-oriented IT landscape, but also harbours a wide range of risks in the areas of security and compliance. Meeting these challenges requires companies to have an appropriate level of risk awareness as well as comprehensive knowledge and effective concepts for active risk minimisation. Our experience shows that many IT managers are reluctant to move completely to the cloud, both for security and financial reasons, and continue to rely on proven and efficient on-prem solutions within their IT asset management, at least in some areas.
Risk minimisation through hybrid cloud or on-prem solutions
Especially in industries with high standards in terms of compliance and data protection, such as energy, healthcare, transport and logistics or waste disposal, but also in the area of public administration, the risks of total cloud solutions are still too high for many IT managers. Instead, hybrid cloud architectures or complete on-premise solutions are being used, in which cloud-specific security risks can be ruled out for at least some areas. In addition, these scenarios open up the possibility of sustainably reducing ongoing licence costs through the needs-based integration of used software, as the following example from the LMT Group shows:
The company from the special machine construction sector with 2,200 PC seats wanted to procure the necessary licences as required. This involved 10 IT locations worldwide. Among other things, the solution combined an Office 365 E1 plan with used licences for Office 2016 and Windows 2016 Server CAL. The result was the functionality of an E3 plan, but without Office ProPlus.
Result: The company achieved savings in the upper six-figure range without any loss of productivity. The investment is amortised in the second year. You can find the entire customer case here.
Convincing advantages - why used software from PREO is worthwhile
We are one of the pioneers in the European trade in used software licences and the market leader in Germany. We offer companies, organisations and public administrations a large selection of used volume licences at any time, especially from major providers such as Microsoft, Adobe, Oracle or Citrix, with which they can sustainably optimise their licence costs and benefit in several ways:
- High savings on ongoing licence costs of up to 70 percent compared to the respective new version.
- Greater sustainability in the IT sector by promoting an active circular economy and reducing the company's CO2 footprint.
- 100 per cent legally compliant and audit-proof licence acquisition with maximum transparency in all processing steps, including complete documentation in the PREO licence portal "Easy Compliance".
- Many years of expertise in the integration of used software licences into classic network structures or hybrid licence models.
- Detailed market knowledge and extensive experience through the audit-proof transfer of over one million used software licences.
- Existing software licence management capacities for large IT infrastructure projects with thousands of workstations and cross-border locations.
- Convincing reference projects for numerous medium-sized and large companies from a wide range of industries.
*see https://www.bsi.bund.de/EN/Themen/Unternehmen-und-Organisationen/Informationen-und-Empfehlungen/Empfehlungen-nach-Angriffszielen/Cloud-Computing/Kriterienkatalog-C5/kriterienkatalog-c5_node.html









